Understanding Cryptocurrency OSINT Attack Surfaces for Better Security
Written on
Chapter 1: Introduction to Cryptocurrency OSINT Attack Surfaces
Cryptocurrency platforms require advanced security measures to safeguard against cyber threats. A significant area of concern is the Open Source Intelligence (OSINT) attack surface. This concept encompasses the publicly accessible data that can be exploited for attacks on cryptocurrency systems. OSINT operations aim to gather information from available sources using sophisticated techniques to sift through the extensive data landscape to pinpoint the information needed for malicious goals.
The OSINT attack surface poses a particular risk within the cryptocurrency realm due to the possibility of sensitive data being revealed. Such information can include wallet details, transaction histories, user identities, and more. By collecting and interpreting this data, cybercriminals can uncover critical insights into a cryptocurrency system's security and identify vulnerabilities to target.
To safeguard these systems, it is crucial to implement comprehensive security strategies that restrict the availability of sensitive public information. This may involve employing strong encryption, enforcing multi-factor authentication, and limiting access to sensitive data to authorized users only. Additionally, organizations should conduct regular security audits to detect and rectify potential vulnerabilities before they can be exploited.
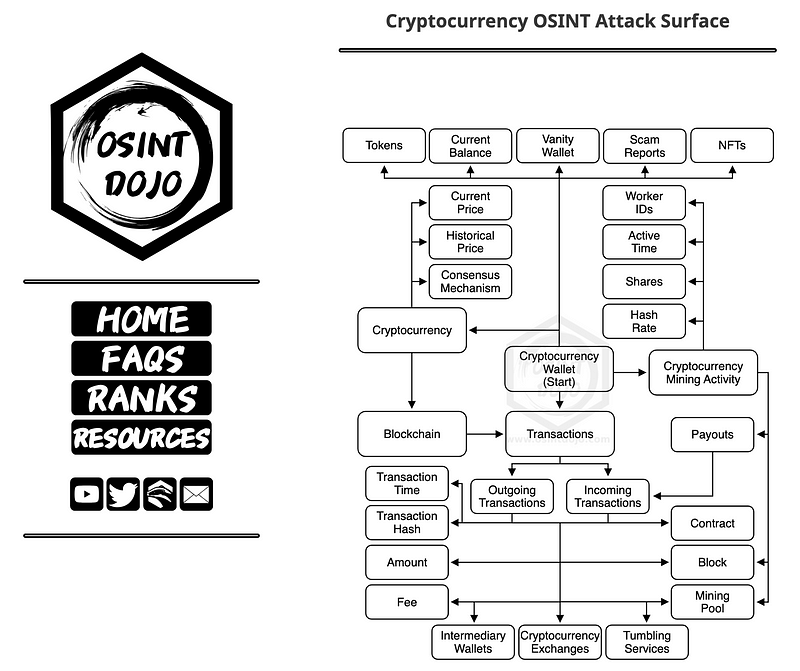
Chapter 2: Strategies for Protecting Against Cryptocurrency OSINT Attacks
OSINT Attack Surface Diagrams V2 Release - This video delves into the methodologies for visualizing OSINT attack surfaces and emphasizes the importance of diagramming in identifying potential vulnerabilities in cryptocurrency systems.
To shield yourself or your organization from the threats posed by the OSINT attack surface in cryptocurrency, it is vital to take proactive cybersecurity measures. Below are several effective strategies:
Username Correlation:
This technique involves matching usernames across various platforms to uncover connections. It can assist in identifying the attacker and tracking their online behavior. However, this method is only reliable if the perpetrator is not concealing their identity with different usernames.
Utilizing OSINT Tools:
OSINT tools can reveal information about yourself, your organization, employees, IT assets, and other sensitive data that could be exploited by adversaries. These tools can scan social media, blogs, forums, and other online platforms to detect malicious activities or information leaks. They can also help you monitor your organization's online reputation and take corrective actions when necessary.
Understanding Cybercriminal Behavior:
To effectively thwart attacks, it is crucial to comprehend the mindset and tactics of cybercriminals. Malicious actors often use multiple usernames across various markets, forums, and chat rooms to evade detection. Utilizing extensive dark web collection tools can help correlate these profiles and extract insights from numerous sources. By recognizing patterns in the attackers' behavior, you can implement preemptive measures accordingly.
By applying these methods, you can enhance your organization's cybersecurity posture and preemptively thwart attacks. The key to effective protection lies in understanding the threat landscape and actively implementing security strategies.

Chapter 3: Conclusion on Cryptocurrency OSINT Attack Surfaces
Lifting the Fog: Investigating Cryptocurrency with OSINT - This video explores how OSINT can be leveraged to investigate cryptocurrency transactions, providing insights into fraud and money laundering practices.
The Cryptocurrency OSINT Attack Surface is a multifaceted aspect of the digital threat landscape. OSINT involves collecting, analyzing, and using publicly available information to identify potential security weaknesses. In the cryptocurrency context, the OSINT attack surface refers to the various methods by which criminals can exploit publicly accessible information to compromise security and gain unauthorized access to cryptocurrency platforms.
Criminals can employ numerous tactics to target cryptocurrency systems through OSINT. For instance, they might utilize social engineering techniques to access user accounts or passwords, or leverage publicly available data to identify weaknesses in cryptocurrency wallets or exchanges. Additionally, attackers may map the cryptocurrency ecosystem to identify key players or platforms to target.
To defend against OSINT attacks, it is crucial to understand how criminals exploit publicly available information. This includes being aware of common social engineering techniques, maintaining robust passwords and security protocols, and staying informed about the latest security threats and trends.
By remaining vigilant and informed, you can minimize the risk of OSINT attacks and help ensure the security and integrity of cryptocurrency assets.
More Info & Links Below:
Stay safe online and keep learning about OSINT and cryptocurrency security!
